KYC Kiosk News
What is electronic KYC? eKYC is the expression used to describe the digitalization and electronic and online conception of KYC processes. eKYC (Electronic Know Your Customer) is the remote, paperless process that minimizes the costs and traditional bureaucracy necessary in KYC processes. Our newest gold-level sponsor IDmission is an expert at KYC solutions.
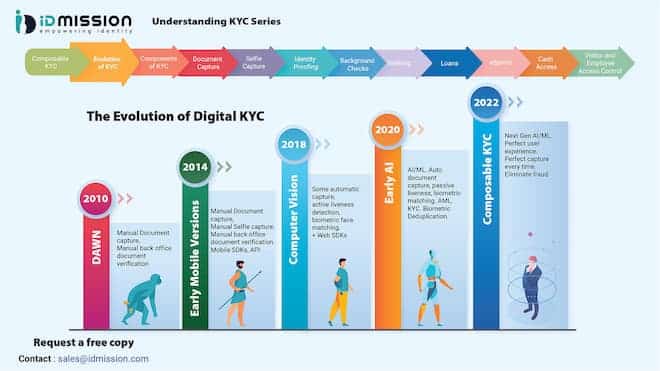
See blog on IDmission on evolution of KYC — for free copy contact [email protected] – IDmission, a global leader in biometric and AI technology, reduces risk associated with false identities. We are the sole provider of a proprietary, end-to-end biometric solution for identity theft, through a comprehensive KYC platform and automatic ID document analysis across 200 countries and four categories of biometrics: face, fingerprint, iris, and voice.
Convenience vs. Security: The Perennial Tug-of-War in KYC
We have come a long way in the evolution of KYC. For the longest time, traditional rules-based KYC and AML efforts were slow, manual, and mired in bureaucracy. Even now, many financial institutions find themselves trapped in a dilemma: the perennial tug-of-war between user convenience and security. Business and security leaders in the digital identity space continue to look for some kind of middle ground while hoping the trade offs are worth it.
However, advances in Artificial Intelligence (AI) and biometrics technology present a way out of this dilemma. Identity proofing, which is one of the key pillars of KYC, has reached the next level where convenience and security are complementary. To understand how this is possible, we must first look at the three factors of authentication and the varying levels of security of each factor. When it comes to access control, the three authentication factors are:
- Possession – something only the user has; authentication by a credit card or smartphone
- Knowledge – something only the user knows; authentication by a password or PIN
- Biometrics – something only the user is; authentication by facial recognition or a unique physical characteristic like a fingerprint
Authentication by either possession or knowledge alone is risky because both can be stolen and misused by a bad actor. To address this security risk, organizations turn to multi-factor authentication, a practice that requires users to identify themselves by more than a username and password – in other words, by more than just knowledge-based authentication. One misconception is that multi-factor authentication involves multiple steps of authentication, such as asking for a username, for a password, and security questions. This, in fact, is not multi-factor authentication, because all the steps are still just testing the person’s knowledge. Multi-factor authentication requires testing at least two different factors, not multiple questions/tests for one factor. A good example of two-factor authentication is money withdrawal from an ATM, where only the correct combination of a bank card (something the user possesses) and a PIN (something the user knows) allows the transaction to be carried out.
Biometrics is the most secure factor of authentication, because faces and fingerprints are extremely difficult to steal or recreate. Up until recently, the challenge had been in waiting for technology to catch up to make biometric authentication more accurate and frictionless. Now, thanks to advancements in reliable AI and biometric technology, biometric authentication is widely considered not only the most secure, but also – when done right – the most convenient form of authentication.
Passive Liveness & Biometric Deduplication: How AI and Biometrics have made it possible for security and UX to be complementary in identity proofing
Technological developments in AI and biometrics have revolutionized the fight against fraud and identity theft. We explore this in two main scenarios that bad actors can perpetrate fraud.
Scenario 1: Fraudster steals a wallet
One of the most common cases of identity theft occurs when a fraudster steals an ID document. Let us call this the scenario of a stolen wallet.
The fraudster takes the ID, goes onto Facebook and searches the name of the ID’s owner, and downloads a photo of the person. Then, the fraudster tries to open a fake account or access the ID owner’s bank account online. When the fraudster reaches the identity proofing process, they show the stolen ID document to pass the document authentication step, and then they present the Facebook photo for the selfie-to-document match authentication step.
However, the fraudster’s attempts would be thwarted. The advances in AI and biometric technologies have taken the security of liveness detection to the next level. The software can automatically detect and reject presentation attacks including photos from phone or laptop screens, print-outs and photographs (color or black & white), masks, face busts, statues, and deep fakes.
Not only has AI and biometric technologies elevated the security of liveness detection, but it has also made the process easier for users with passive liveness detection. The earlier generation of facial liveness detection technology, referred to as “active” liveness detection, relied on the user’s movements in response to prompts such as nodding, blinking, smiling, or turning their head left or right (which would sometimes create confusion for the user and lead to abandonment). In contrast, passive liveness detection is much more convenient.
Many vendors claim to have passive liveness, yet the end user still has to zoom the phone in and out to prove liveness. IDmission’s passive liveness detection is totally frictionless with a snap-and-go technology. Unlike other vendors, we do not have to send the image up to a server to determine liveness. We do it in a split second right from the user’s phone.
Now, let us say that our fraudster is determined to find a workaround to the liveness detection. They decide to present their own face for the liveness detection stage in the identity proofing step and alter the ID document to include the fraudster’s photo. This brings us to scenario 2.
Scenario 2: Fraudster steals many wallets
In scenario 2, our fraudster has stolen multiple ID documents or otherwise gets access to photos of multiple people’s IDs. The fraudster puts these photos into Photoshop one by one and edits their own selfie onto the ID photos. Then, they print out the edited document images, and proceed to open fake accounts or access the owners’ accounts with the tampered IDs. However, the fraudster would run into two key obstacles.
Firstly, AI-powered technological advancements have enhanced the security of document capture capabilities. The best-in-class identity proofing software does not allow capture of ID images from screens and printouts (in color or black & white).
Secondly, biometric deduplication prevents the fraudster from opening more than one account with their biometrics. Biometric deduplication is the procedure used to create and manage a unique set of biometrics of a person within a system. Biometric deduplication plays a vital security role in the enrollment process by comparing the biometric information of the enrolling individual against the biometric data of all previously enrolled individuals. This prevents identity duplication, which – in more benign cases – could be an unintentional mistake where a person’s data was entered multiple times within the system. In more malign cases, the technology quickly catches a fraudster who is using the same face multiple times to create or access different accounts.
In Gartner’s Market Guide for Identity Proofing and Affirmation (2022), analyst Akif Khan stresses the importance of balancing “the often competing demands of trust, compliance and UX” which often requires “a layered approach of multiple capabilities”. IDmission has been included in Gartner’s list of representative vendors for the fifth year in a row, as an identity proofing solution provider that manages risk across the user journey while optimizing UX.
Over the upcoming weeks, as part of our Understanding KYC Series, we will be taking a closer look at each of the key technology components that make up a best-in-class identity proofing solution that strikes a balance between security, compliance, and user experience.
Examples
Automated Bar for Sports Fans w/ Facial Recognition & Age Verification
Automated Bar Service News IDmission brings verification, convenience, and security to TendedBar automated cocktail service Jacksonville, FL – Whether it’s an NFL Game, an Elton John, Metallica, or Bruno Mars concert, or the final round of a PGA TOUR event, the last thing fans want to do is miss the action while waiting in line to get a drink. TendedBar,… Read More »
About IDmission
IDmission, a global leader in biometric and AI technology, reduces risk associated with false identities. We are the sole provider of a proprietary, end-to-end biometric solution for identity theft, through a comprehensive KYC platform and automatic ID document analysis across 200 countries and four categories of biometrics: face, fingerprint, iris, and voice. For more information, contact [email protected].
Facial Recognition,Biometrics,passive liveness
More Posts


